Counter And Defense Against RAT Attack
Welcome to the third part of The RAT tutorial and I am extremely sorry you have to wait a little more so see this article coming up. By the way in this section we ll make ourselves aware how we can counter and create a defense against RAT attack. Dear visitor if you are reading this post without reading its previous parts then I urge you to please read,
before you read this.
So as seen before RAT may use any unknown port to communicate with attacker and the best defense against any process communicating using unknown port is firewall. There are various commercial firewalls available but here are few good free firewalls that can even lead a commercial firewall bow down to its feet. Following are few good free firewall programs on basis of their ranking by customers,
1.Online Armour
2.Zone Alarm
3.Comodo Firewall
4.Private Firewall
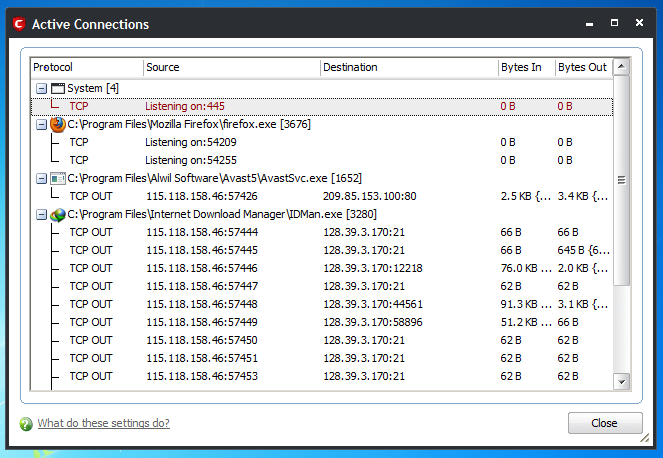
People consider Online Armour as one of the toughest free firewall available, by the way I prefer Comodo Firewall. Comodo firewall also shows you process which are communicating, port numbers via which they are communicating and full path of process invoking executable file, here's a view of how Comodo shows you process.
Now as we discussed in RAT - II a RAT becomes fully undetectable if he/she applies any process discussed in previous RAT post. That means if your anti-virus fails to detect it, following can be symptoms that can appear on your system which can help you identify its presence,
1.Disable Of Task Manager and Disable Of Folder Option
2.Sudden Opening And Closing Of CD/DVD-ROM
3.Blue Screen Of Death or Just Blue Screen
4.High Bandwidth Consumption
5.Sudden Open Of Web Pages
6.Pop Ups
7.Change Of Wallpaper
8.Disappear Of Mouse Arrow, Start Button and Task Manager
If you find any of the above things happening on your PC its time to manually check your system for RAT. But as I told you before RAT server may hide in known processes or may even use only known ports to communicate with attacker so detection would not be easy. Here we'll learn step by step approach how you can manually detect its presence.
As told earlier a RAT can hide it self in process space of another process like explorer.exe, iexplorer.exe, scvhost.exe, services.exe. Open your firewall and check out if explorer.exe or services.exe are communicating with remote host. If yes then you are infected because these processes never communicate with any remote host. Now the process that communicate are svchost.exe and iexplorer.exe.
To find out whether iexplorer.exe is communicating with remote host as client to installed RAT server close Internet Explorer, wait for 5-6 seconds and see if its communicating then you are infected. Now if attacker has configured to close connection as soon as Internet Explorer(IE) closes you will not be able to detect its presence in firewall, in this case you have to keep yourself prepared by watching how much memory IE takes while opening www.google.com leave IE like that and open “Task Manager” by typing taskmgr.exe in RUN window. Keep your eye on memory consumption(not CPU consumption) of IE if it fluctuates even after 1 minute then you can be sure you are 100% infected.
What if attacker decides to hide process in scvhost.exe? In this case open firewall and watch for ports with which svchost.exe is communicating. Make sure port numbers should be 53 or 443 on remote host in listening mode only, if not then you are infected. Now if attacker has planted port number 53 or 443 in RAT for communication with svchost.exe then how you gonna detect. Now here you'll need a little technical brain, a scvhost.exe process runs in three modes,
System Mode: Which never communicates with internet
Local Mode: Which never communicates with internet
Network Mode: Which communicates with internet.
All three modes run as different processes with different process IDs. Now the Network Mode scvhost.exe runs as network service, so open taskmgr.exe and locate scvhost.exe where username is Network Service now note process ID, disconnect from network and wait for 1-5 minute monitoring that process memory consumption. You have to wait for 5 minutes just because even after disconnecting scvhost.exe does not settle down network and hence memory usage appears fluctuating for long time. Once memory usage becomes stable then wait for sometime and monitor it for memory usage fluctuation, it should not be above 2 MBs.
Now above were manual method to identify presence of RAT in your system if your Anti-Virus and even malware detection software fails to detect RAT. So far as my view is concerned Norton, Avast Professional, Avira and AVG professional are best Security Suites available to tackle all kind of software based threats and malware. And if you use your system for critical purposes then you are the fellow who is in very much need of “Black Ice Defender”. It is awesome piece of code written specially to avoid any kind of intrusion on your system.




21 comments
I'm here representing the visitors and readers of your own website say many thanks for many remarkable
angularjs Training in bangalore
angularjs Training in electronic-city
angularjs Training in online
angularjs Training in marathahalli
Posted on September 25, 2018 at 11:41 PM
Thank you a lot for providing individuals with a very spectacular possibility to read critical reviews from this site.
Python training in marathahalli | Python training institute in pune
Posted on October 12, 2018 at 10:43 PM
Nice post. By reading your blog, i get inspired and this provides some useful information. Thank you for posting this exclusive post for our vision.
Data Science Training in Chennai | Data Science training in anna nagar
Data Science training in chennai | Data science training in Bangalore
Data Science training in marathahalli | Data Science training in btm layout
Posted on October 17, 2018 at 10:49 PM
Thanks for providing wonderful information with us. Thank you so much.
Regards,
PHP Training in Chennai | PHP Course in Chennai
Posted on January 27, 2019 at 2:19 AM
This is quite educational arrange. It has famous breeding about what I rarity to vouch. Colossal proverb. This trumpet is a famous tone to nab to troths. Congratulations on a career well achieved. This arrange is synchronous s informative impolites festivity to pity. I appreciated what you ok extremely here
devops online training
aws online training
data science with python online training
data science online training
rpa online training
Posted on March 13, 2019 at 12:33 AM
Do you need a hacker, is your spouse cheating on you? Do you want to track him/her ? For all forms of hacking, contact:+16677772490
website: https://www.wiki-spy.com/ Satisfaction Guaranteed and prompt delivery on all of our services.
We have a professional hacker suitable for all of your needs
Your anonymity matters to us
Posted on May 21, 2019 at 4:23 AM
Thanks for providing wonderful information with us.
Yaaron Studios is one of the rapidly growing editing studios in Hyderabad. We are the best Video Editing services in Hyderabad. We provides best graphic works like logo reveals, corporate presentation Etc. And also we gives the best Outdoor/Indoor shoots and Ad Making services.
Best video editing services in Hyderabad,ameerpet
Best Graphic Designing services in Hyderabad,ameerpet
Best Ad Making services in Hyderabad,ameerpet
Posted on September 15, 2019 at 11:12 PM
ACTIVE & FRESH CC FULLZ WITH BALANCE
Price $5 per each CC
DETAILS
=>CARD TYPE
=>FIRST NAME & LAST NAME
=>CC NUMBER
=>EXPIRY DATE
=>CVV
=>FULL ADDRESS (ZIP CODE, CITY/TOWN, STATE)
=>PHONE NUMBER,DOB,SSN
=>MOTHER'S MAIDEN NAME
=>VERIFIED BY VISA
=>CVV2
*Time wasters or cheap questioners please stay away
*You can buy for your specific states too
*Payment in advance
Contact Us:
-->Whatsapp > +923172721122
-->Email > leads.sellers1212@gmail.com
-->Telegram > @leadsupplier
-->ICQ > 752822040
US FRESH, TESTED & VERIFIED SSN LEADS
$1 PER EACH
(INFO)
First Name | Last Name | SSN | Dob | Address | State | City | Zip | Phone Number | Account Number | Bank NAME | DL Number |
Home Owner | IP Address | MMN | Income
*Hope for the long term deal
*If anyone need leads In bulk, I'll definetly negotiate
US DUMP TRACK 1 & 2 WTIH PIN CODES ALSO AVAILABLE
Posted on June 13, 2020 at 12:28 PM
I never get bored while reading your article because, they are becomes a more and more interesting from the starting lines until the end. thank you for useful information.
python training in chennai
python online training in chennai
python training in bangalore
python training in hyderabad
python online training
python flask training
python flask online training
python training in coimbatore
Posted on July 22, 2020 at 1:09 AM
If you are in need of financial Help, don't hesitate to place order for deserve Programmed card that can withdraw any amount limit you want. Deserve Card are very transparent and easy to deal with. You can Purchase Deserve card that can withdraw up to $50,000 to $100,000 limit without being detected because of the programming of the card. I'm extremely grateful to them for being honest with their words and delivering the card to me. This is the third day of receiving the card and i have withdraw $9,500 from the Deserve Programmed Card. I tried purchasing the card previously from someone else, but it never arrived until i tried skylink technology for those in need of more money, you can also contact them. you can place order for the card Via whatsapp/telegram +1(213)785-1553 or their E-mail: skylinktechnes@yahoo.com
Posted on September 1, 2020 at 6:06 AM
Selling USA FRESH SSN Leads/Fullz, along with Driving License/ID Number with good connectivity.
**PRICE FOR ONE LEAD/FULLZ 2$**
All SSN's are Tested & Verified. Fresh spammed data.
**DETAILS IN LEADS/FULLZ**
->FULL NAME
->SSN
->DATE OF BIRTH
->DRIVING LICENSE NUMBER
->ADDRESS WITH ZIP
->PHONE NUMBER, EMAIL
->EMPLOYEE DETAILS
->Bulk order negotiable
->Minimum buy 25 to 30 leads/fullz
->Hope for the long term business
->You can asked for specific states too
**Contact 24/7**
Whatsapp > +923172721122
Email > leads.sellers1212@gmail.com
Telegram > @leadsupplier
ICQ > 752822040
Posted on October 9, 2020 at 7:03 PM
Selling USA FRESH SPAMMED SSN Leads/Fullz, along with Driving License/ID Number with EXCELLENT connectivity.
**PRICE**
>>2$ FOR EACH LEAD/FULLZ/PROFILE
>>5$ FOR EACH PREMIUM LEAD/FULLZ/PROFILE
**DETAILS IN EACH LEAD/FULLZ**
->FULL NAME
->SSN
->DATE OF BIRTH
->DRIVING LICENSE NUMBER WITH EXPIRY DATE
->ADDRESS WITH ZIP
->PHONE NUMBER, EMAIL, I.P ADDRESS
->EMPLOYEE DETAILS
->REALTIONSHIP DETAILS
->MORTGAGE INFO
->BANK ACCOUNT DETAILS
>All Leads are Tested & Verified.
>Invalid info found, will be replaced.
>Serious buyers will be welcome & I will give discounts for bulk orders.
>Fresh spammed data of USA Credit Bureau
>Good credit Scores, 700 minimum scores
>Bulk order will be preferable
>Minimum order 20 leads/fullz
>Hope for the long term business
>You can asked for samples, specific states & zips (if needed)
>Payment mode BTC, PAYPAL & PERFECT MONEY
Email > leads.sellers1212@gmail.com
Telegram > @leadsupplier
ICQ > 752822040
''OTHER GADGETS PROVIDING''
>Dead Fullz
>Carding Tutorials
>Hacking Tutorials
>SMTP Linux Root
>DUMPS with pins track 1 and 2
>Sock Tools
>Server I.P's
>USA emails with passwords (bulk order preferable)
**Contact 24/7**
Email > leads.sellers1212@gmail.com
Telegram > @leadsupplier
ICQ > 752822040
Posted on January 13, 2021 at 12:28 PM
This article are supper help full if you want to now more about How to Activate PNC Credit Card then please click
Posted on February 9, 2021 at 9:12 AM
**SELLING SSN+DOB FULLZ**
CONTACT
Telegram > @leadsupplier
ICQ > 752822040
Email > leads.sellers1212@gmail.com
>>1$ each without DL/ID number
>>2$ each with DL
>>5$ each for premium (also included relative info)
*Will reduce price if buying in bulk
*Hope for a long term business
FORMAT OF LEADS/FULLZ/PROS
->FULL NAME
->SSN
->DATE OF BIRTH
->DRIVING LICENSE NUMBER WITH EXPIRY DATE
->COMPLETE ADDRESS
->PHONE NUMBER, EMAIL, I.P ADDRESS
->EMPLOYMENT DETAILS
->REALTIONSHIP DETAILS
->MORTGAGE INFO
->BANK ACCOUNT DETAILS
>Fresh Leads for tax returns & w-2 form filling
>Payment mode BTC, ETH, LTC, PayPal, USDT & PERFECT MONEY
''OTHER GADGETS PROVIDING''
>SSN+DOB Fullz
>CC with CVV
>Photo ID's
>Dead Fullz
>Spamming Tutorials
>Carding Tutorials
>Hacking Tutorials
>SMTP Linux Root
>DUMPS with pins track 1 and 2
>Sock Tools
>Server I.P's
>HQ Emails with passwords
Email > leads.sellers1212@gmail.com
Telegram > @leadsupplier
ICQ > 752822040
THANK YOU
Posted on March 26, 2021 at 7:05 PM
Very informative blog Thank you for sharing.
Microsoft MSBI Certification Training in Chennai
Informatica Certification Training in Chennai
Docker Training in Chennai
Android Application Training In Chennai
Ios Application Training In Chennai
Best Software training institute
Xamarin Training in Chennai
Power-Bi Certification Training
Posted on October 21, 2021 at 5:18 AM
Expecting mothers trust KKCTH as the best maternity hospital for normal delivery in chennai. Their team of highly qualified doctors and nurses ensures minimal medical interventions while providing a comfortable and safe environment for childbirth.
Posted on March 3, 2025 at 10:56 PM
Whether it's kidney stones, infections, or prostate issues, the best urologist in Chennai provides comprehensive care with the latest technology. Trust an experienced specialist for safe and effective treatment options tailored to your condition.
Posted on May 22, 2025 at 11:22 PM
NICE BLOG
safety course in chennai
Posted on June 20, 2025 at 4:25 AM
NICE ARTICLE
safety course in chennai
Posted on June 21, 2025 at 3:08 AM
Loved this post
safety course in chennai
safety course in chennai
Posted on June 22, 2025 at 10:26 PM
Useful Article!
safety course in chennai
safety course in chennai
Posted on November 29, 2025 at 2:49 AM